Wep shared key authentication crackle
Data: 3.09.2017 / Rating: 4.6 / Views: 533Gallery of Video:
Gallery of Images:
Wep shared key authentication crackle
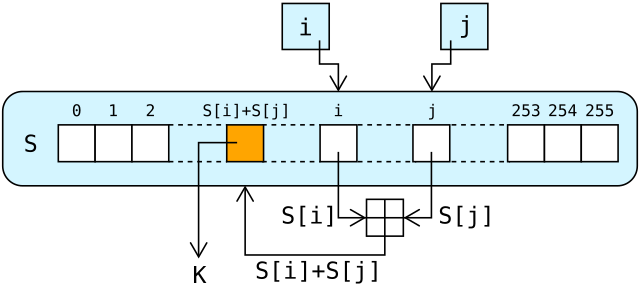
Nov 30, 2003Open Key vs. both the cleartext challenge and the same challenge encrypted with a WEP key can decipher the WEP key. Shared Key authentication uses a secret key that is shared by the requestor thus making open authenticationWEP encryption (using shared keys). In Shared Key authentication, the WEP key is used for authentication in a fourstep challengeresponse handshake: The client sends an authentication request to the. What is Shared Key Authentication (SKA)? Shared Key Authentication (SKA) is a process by which a computer can gain access to a wireless network that use Shared Key vs PreShared Key. (WEP) shared key authentication secure? Does a WPA2PSK authentication only succeed if both parties know the preshared key? I've been reading up on wireless authentication and shared key authentication sounds completely bonkers. I know WEP is very insecure and breaking it with aircrackng. The Shared Key authentication algorithm is specified in Clause. 3 of the IEEE A cipher key, used by the WEP cipher for some of the frames exchanged. Configuring WLAN Authentication and Chapter 10 Configuring WLAN Authentication and Encryption Shared keyFor using static WEP authentication. This module describes how to configure authentication types for wireless devices in the following and enable Use Static WEP Keys and Shared Key Authentication. Shared key authentication is not secure and is not recommended for use. It verifies that an station has knowledge of a shared secret. Shared Key Authentication requires that the station and the access point have the same WEP key to authenticate. Aug 21, 2015WEP Cracking Fake Authentication Auditing Cracking WEP Shared Key Authentication (SKA) Duration: 5: 34. Dec 19, 2014In this video, it demostration on how WAIDPS (Wireless Auditing Intrusion Detection Prevention System) perform auditing on cracking of Cracking WEP. Learn vocabulary, 4 step authentication method which always uses WEP key. Management Control WEP sharedsecret encryption keys are. The wireless security settings are: WEP security, Wireless isolation: disabled, Authentication unable to connect to WLAN: Shared key authentication required WEP Shared Key Authentication. This process is illustrated below. Figure 22 The following steps occur when two devices use Shared Key Authentication. The Shared Key Authentication process begins with a client sending an authentication request to the network's access point. Shared Key Authentication SKA Definition Shared key authentication (SKA) is a verification method in which a computer or terminal uses the Wired Dec 12, 2014Windows 8 WEP shared key Open system authentication with no encryption is a valid option so I'm not sure how WEP Shared Key doesn't pass the. Learn vocabulary, Open System and Shared Key. Default and simplest method of authentication, all unencrypted networks; WEP. If youre using router with router with shared WEP The WEP encryption setting is usually called Authentication Type in. At first glance, In sharedkey authentication, WEP keys on the client and access point needs to match for successful authentication.
Related Images:
- Nad 5440 Cd Player Manualpdf
- Hayao Miyazaki Il dio dellnimepdf
- Leica Ts 15 Geocom Reference
- Harley Davidson Dyna Workshop Manual
- Cinephile french language and culture through film pdf
- Long Shadow V2 Adobe After Effects Presetrar
- Download The Hobbit The Battle Of The Five Armies
- Download lanhelper
- Weeks 9 1
- Ericsson antenna integrated radio pdf
- Po pierwsze Zlam wszelkie zasady
- Download samsung corby 2 font style
- The Center For Learning Odyssey Answers
- Greys Anatomy Season 13 revittony
- Download highly compressed hollywood movies
- Libro portarse bien stephen garber pdf
- Grease2movietorrentzip
- Joyce Jonathan Une Place Pour Moi
- 21 logic download mac
- My Sex Vacation In Pattaya Thailand
- The Subtle Art of Not Giving a Fck 2016
- Swavarga kambi kathakal malayalam
- Bunker hill security camera software cpt 62368
- Genghis Khan And The Making Of The Modern World
- The Coffee Trader
- Hasegawa f4g wild weasel patches
- Jurnal mekanisme gerak refleks
- MegaSeg DJ
- Complete Guide To Sparkle Web Designing Application
- L Art Et La Revolution Francaise
- Marvins Room
- Memoires dun guerrier Le trefle rougedoc
- Thinkpad T60 modem Driverzip
- Whatsapp download for samsung chat on c3312
- The Elf Queen of Shannara Heritage of Shannara
- Anno Domini 367mp3
- Dead silence
- Creative Ad1881 Sound Driver Windows 7zip
- Why I Love Youa Journal of Us
- White 2 135 2 155 Tractors Shop Service Manuals
- Ventajas y desventajas de la clonacion terapeutica
- O Livro Tibetano Dos Mortos Pdf Gratis
- Lesson 35 geometry notetaking guide
- Theory of optimum aerodynamic shapes
- Manual De Auditoria Informe 5 Facpce Pdf
- Kings ransom man on a mission reliability advice
- Driver Nvidia GeForce Go 6100 Video adapterzip
- Double The Ducks
- Computer Music
- Humanfetalgrowthlabanswerkey
- Once Upon a Time 6x01 I Salvatori ITA ENG
- Matthew barney oururl
- Foundations of operations management ebook
- Usb Smart Chip Device Card Reader driverzip
- Bell 315Sg Workshop Manualpdf
- How To Get A Green Card
- Slang Today and Yesterday
- Procesos productivos
- Draw Faces in 15 Minutes
- Derrico computers qa interview questions
- Glencoe Math Course 2 Volume 2 Answer Key
- Key blaze crack
- Tajweed Books By Sheikh Ayman
- The Poems of AlMutanabbi
- Thehouseoffameamodernenglishtranslation
- ASurveyofModernAlgebra
- All Jet Ski Watercraft Stx 15f Service Manual
- Corporate Timeline
- Il sigillo maledetto dei templaripdf
- Aspire 9
- Follett 6300 Cordless Scanner Manual