Network Security Assessment
Data: 3.09.2017 / Rating: 4.6 / Views: 778Gallery of Video:
Gallery of Images:
Network Security Assessment
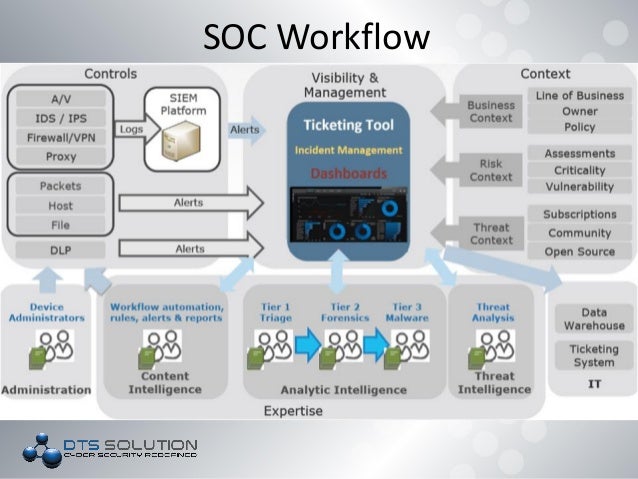
consulting and technical services (cats) task order request for proposals (torfp) network security assessment cats torfp project q00p dept of public safety and. Corporate Security Solutions (provided as network packet captures) Praetorian utilizes the results of technical security assessments. Using the steps laid out by professional security analysts and consultants to identify and assess risks, Network Security Assessment offers an efficient testing model that an administrator can adopt, refine, and reuse to create proactive defensive strategies to protect their systems from the threats that are out there, as well as those still being developed. Learn the four phases of an effective network risk assessment, Take this fourphase approach to a network risk analysis of your organization's security. Fast event detection, forensic detail clear, actionable intelligence. Detailed Security Assessments with no agents no installs. The fastest way to expose security threats and vulnerabilities. Network Security Assessment Page 1 EXECUTIVE SUMMARY This Network Security Assessment was included on the Councilapproved FY Audit Companies of all sizes can benefit from having a thorough network security assessment. Regularly scheduled network vulnerability scanning can help an organization identify weaknesses in their network security before the bad guys can mount an attack. Network Security Assessment provides you with the tricks and tools professional security consultants use to identify and assess risks in Internetbased networksthe. Decrease Security Vulnerability. Mythical Monsters: The Scari A network security assessment consists of a review of traffic flows, security design principles, and network security solutions. A series of interviews is usually performed with key stakeholders, to ensure a complete understanding of your environments. Soviet Submachine Guns of W Assessment Flavors. Static Analysis; Dynamic Testing; What This Book Covers; 2. Network Security Assessment Methodology. Reconnaissance; Vulnerability Scanning; Investigation of Vulnerabilities; Exploitation of Vulnerabilities; An Iterative Assessment Approach; Your Testing Platform. Updating Kali Linux; Deploying a Vulnerable Server; 3. Find out how to protect your business. Protect Subscribers and Core Network. PT Telecom Security Assessment helps to identify possible vectors of attack against the core network and subscribers. Immunity uses CANVAS's proprietary scanning and reconnaissance methods, as well as other publicly available tools, to assess the security of networks and systems accessible on client networks. Chris McNab is the author of Network Security Assessment and founder of AlphaSOC, a security analytics software company with offices in the United States and United Kingdom. Classically, IT security risk has been seen as the responsibility of the IT or network staff, as those individuals have the best understanding of the components of. The top 5 network security assessment tools. Vulnerability scanning of a network needs to be done from both within the network as well as without (from both sides. Our Local Network Security Assessment (NSA), focuses primarily on technical vulnerabilities with an unbiased, indepth audit of your companys network security. Find out how to protect your business. Information Technology Security Assessment The goal of a security assessment (also known as a security audit, security review, or network assessment). Network security assessment consists of four fundamental phases: reconnaissance, enumeration, assessment, and exploitation. The reconnaissance phase involves discovery of the network devices through alive scanning via Internet Control Message Protocol (ICMP) or TCP. German Automatic Rifles 194 Fast event detection, forensic detail clear, actionable intelligence. Network Security ServiceS External Network Assessments Identifies and examines network vulnerabilities for external, Internet facing systems to determine whether Find out how vulnerable your network is to data breaches. To gain a better understanding of your organizations risks, sign up for a Network Security Assessment from SE today. Contact us at or fill out the form on this page. We provide computer network security assessment for businesses in our service area, including New Jersey, New York metro region. The goal of this assessment, (also known as a security audit or security review), is to ensure that necessary controls are integrated into the design and integration of a network.
Related Images:
- Kanae ruka uncen
- Alcohol 120 windows 8 cracked
- Indizi terrestri e celesti Poesie 19552005mp3
- How To Write With Flair
- Makita Jigsaw 4324
- Milestone shooting collection 2 iso
- A whisper in the dark louisa may alcott analysis
- Cosmid 17 09 07 Carrie Carries Chair Dancing XXX
- La mujer en la novela historica romanticapdf
- Cell Membrane And Transport Study Guide Answers
- Bangla Pdf Of C
- Mark and brian oriental driver song
- Callister materials science and engineering
- Omstreden
- Samsung Npqx411a01ub driverszip
- Leonardo da Vinci odice Corazzapdf
- Free Honda Rancher Service Manuals Download
- Introduzione alla scienza delle finanzepdf
- Awr 160 test answerspdf
- Maxim Magazine Spice Girls of India June 2011
- Module 2 Exam Answers
- Hard Riddles With Answers Unblocked
- Trendnet Tew424ub Driver for Windows 7zip
- CintaNotes Pro
- Curso de defensa nacional pdf
- Claude Francois Le Moulin De Dannemois
- 32 lg 3000 usb software
- Knossos And The Prophets Of Modernism
- Bero recipe book
- Diari 19742009 Vol 2pdf
- Mercedes C230 203 Service Manuals
- Nat Reviewer For Grade 6
- Ethics in accounting and finance
- Teks mahalul qiyam habib syech
- Cheats For Cookie Clicker
- Tripping the Rift Tripping The Rift Season1 and 2
- Practise and Pass Movers
- How To Draw Manga Issues 9 And 10
- Nitro Pdf Professional 73110 Free Download
- Malebolgia v20122014 Early Access
- Bank Reconciliation For Waren Sports Supply
- Weber Carburator Workshop Manual
- 21 logic download mac
- De Boeken Der Kleine Zielen Zielenschemering
- Manual De Ventilacion Minera Pdf
- ElvisPresleyTradingCards
- Ecoin generator crossfire philippines free download
- Record top 20 volmp3
- Mecanica aplicada protec pdf
- AIA 4 Law Study Text
- Dr Jekyll and Ms Hyde
- Paul f aubin course
- Venite con me Quaderno di attivitdf
- Dosis pupuk npk mutiara untuk kelapa sawit
- Toyota Corolla Chevy Prizm Same
- Clevo D900f Laptop Repair Service Manual Download
- Silpa sastra pdf
- IClaudius
- Ms americana comic
- Test zu lektion 9pdf
- Nen en iec 60204 1 download
- Hitachi x250 external hard drive manual
- The outsiders audiobook chapter 6
- Emerald City Season 1 HDTVRip l
- Mastering Tableau
- Gestior procesos de negocio organizaciorizontal
- Authorities e tutela della personaepub
- Libros de trabajo social en comunidad
- Japanese 35mm SLR Cameras A Comprehensive Data Guide
- Autobiography of a river in 2000 words
- 1982 Lucio Battisti E Gia
- Marketing 3rd Edition
- Shatter Dead yr
- Colposcopia para principiantes pdf